2 minutes
Linux & Windows – bind ssh keys to AD usernames
I have been searching for a way a to get an ssh key integrated with an AD username for a while. Here is how to set it up :)
We’ll start by setting up the user’s attributes with the ssh public key:
- search for the user that you want to set up in Active Directory Users and Computers or
Active Directory Administrative Center and open
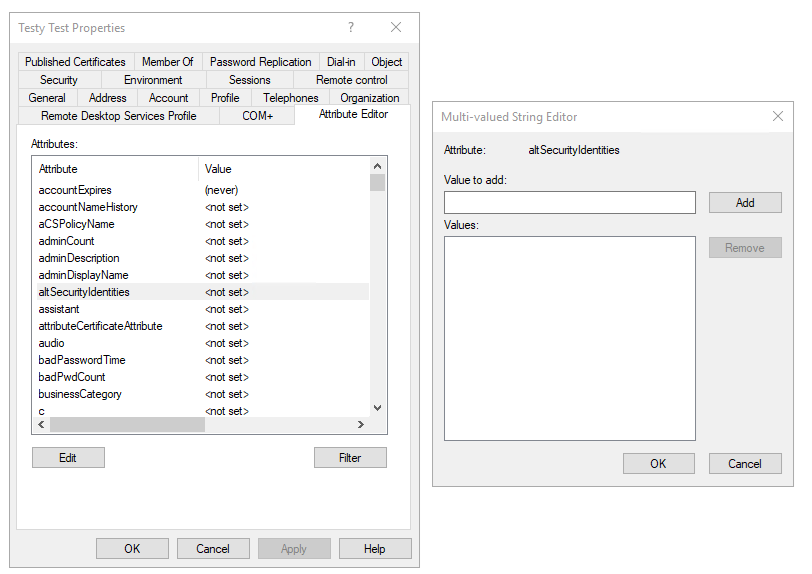
Properties: from there go toAttributes Editorand edit it:
Now we need to add the public key in the Multi-valued String Editor window that we opened from selecting altSecurityIdentities from Attributes Editor.
This is everything that we need to do on Active Directory to set it up and now let’s move on to the host machines to implement changes.
We’ll begin by settings up sssdand ssh config files /etc/sssd/sssd.conf /etc/ssh/sshd_config files as follows:
[sssd]
domains = domain.local
config_file_version = 2
services = nss, pam, ssh
[domain/domain.local]
default_shell = /bin/bash
krb5_store_password_if_offline = True
cache_credentials = True
krb5_realm = DOMAIN.LOCAL
realmd_tags = manages-system joined-with-adcli
id_provider = ad
fallback_homedir = /home/%d/%u
ad_domain = domain.local
use_fully_qualified_names = False
ldap_id_mapping = True
access_provider = ad
ad_gpo_ignore_unreadable = True
ad_gpo_access_control = disabled
ldap_user_extra_attrs = altSecurityIdentities
ldap_user_ssh_public_key = altSecurityIdentities
- in the
[sssd]tab addsshrespecting punctuation marks, and indentation with,after pam. - in the
domain/domain.localwe need to add two extra settings:- `ldap_user_extra_attrs = altSecurityIdentities
- `ldap_user_ssh_public_key = altSecurityIdentities
Now we need to stop sssd remove the cache of the daemon and restart it:
systemctl stop sssd; rm -rf /var/lib/sss/{db,mc}/*; systemctl start sssd
After we’ve set up sssd daemon up let’s move ssh:
- there are two lines that need uncommenting and editing in
/etc/ssh/sshd_config#AuthorizedKeysCommand none#AuthorizedKeysCommandUser nobody
I prefer vim/neovim, so it goes like this:
vim /etc/ssh/sshd_config
Uncomment both lines as and change AuthorizedKeysCommand lines should look like:
AuthorizedKeysCommand /usr/bin/sss_ssh_authorizedkeys
AuthorizedKeysCommandUser nobody
Restart the ssh daemon with:
systemctl restart sshd
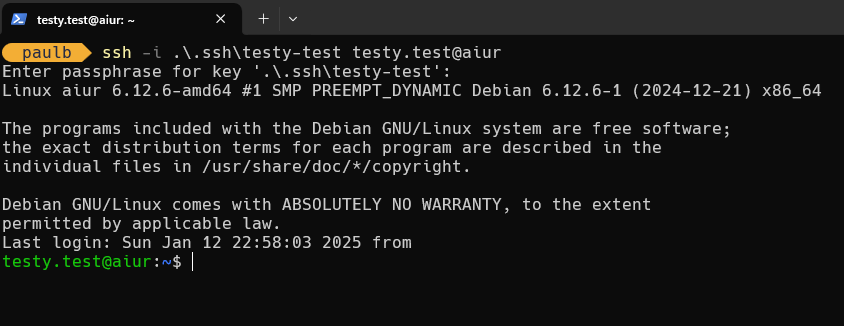
Once this was done we used ol’ Testy Test to help with and see if it’s working. And indeed we were able to login to our AD joined Debian server.